A short and sweet explanation of what SLAM is and how you can protect your business from phishing attacks when you use the SLAM method.
Protecting your business from phishing attacks & phishing emails
Phishing is a type of cyber attack that involves tricking someone into giving up sensitive information, such as passwords, client data, financial data, or for the unsuspecting user to download an attachment or visit a link to infect their computer.
Cybercriminals typically use email as the primary attack vector. However, social engineering phishing like text messages & phone calls/voice mails (known as smishing & vishing) is also commonplace in today’s cyber security landscape.
In this post, we’re going to focus exclusively on email. If you want to know more about social engineering attacks on businesses and have 7 minutes, you should watch the following video of Rachel Tobac, CEO of SocialProof Security. She talks about her time in the booth at Def Con’s Social Engineering Capture the Flag competition and sheds light on how social engineers compromise businesses.
Phishing Attacks In Detail
As mentioned in the intro of this article, this will be a short and sweet explanation of what SLAM is and how your business can implement it.
If you would like to know more in-depth information about phishing, we’ve recently written about it at length in the following posts:
The Three Main Cyber Security Threats and What You Can Do
Spear Phishing vs Phishing: What’s the Difference?
SLAM Acronym
- Sender – Sender’s Email Address
- Links – Where Do The Links Go?
- Attachments – Does The Email Have a File Attachment?
- Message – Does it Make Sense?
Sender – Sender’s Email Address
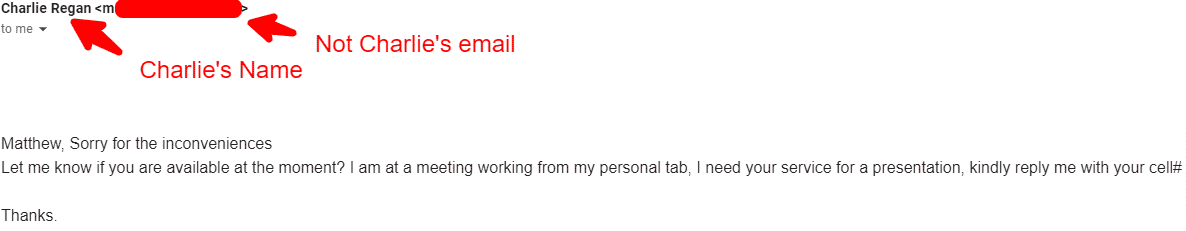
As seen in the image above, showcasing Google’s Gmail, in every email that I receive at the very top, it shows the title, the sender’s name & the sender’s email.
SLAM teaches that you should check the email address every time an email is received, no matter how familiar you are with the sender’s name.
I receive a spear-phishing attempt once a week. The phishing email claims to be from our CEO, Charlie Regan, asking me to take some form of action or provide personal information.
Even though I work closely with Charlie, I check the sender’s email every single time, and these attacks are promptly reported and moved to spam.
Note that the SLAM method should be fully implemented, as the S alone will sometimes not be enough to stop phishing emails. If the sender’s web domain is not configured correctly, cybercriminals can send emails that appear to come from the legitimate sender.
Links: Where Do The Links Go?
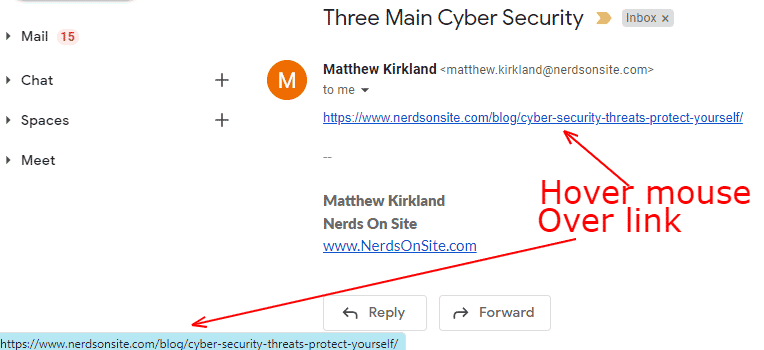
When you hover your mouse over a link, you will see the destination of that link in the bottom left corner of your screen. If this link does not match or does not go where you expect it to go, consider the email suspicious.
Emails don’t just contain text; they are built and displayed using computer code, primarily HyperText Markup Language (HTML).
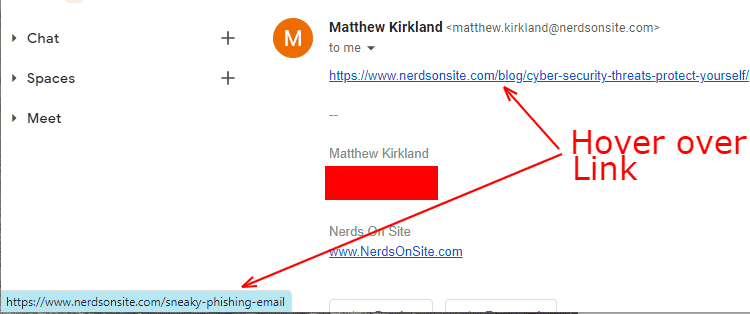
Using HTML, we can make a link display in the email that it’s going to one place but to another. The above example shows the link going to the correct place, but the below example highlights the trickery that some cybercriminals implement.
This step is crucial. Cybercriminals create websites that look like the original to trick you into entering your credentials and then stealing corporate or personal information.
The best way to combat this phishing email is to contact the sender directly by phone and confirm it’s legitimate.
Attachments: Does The Email Have a File Attachment?
Even if you’ve completed S & L, you still need to be vigilant. Phishing emails may come from the correct sender due to a configuration issue or the sender being hacked.
A common method utilized in phishing attacks is sending file attachments that contain malware, ransomware, or other dangerous computer viruses.
Attachments will never be safe. You are allowing a program to execute code on your computer, and by default, this opens you up to the potential for the said program to install malicious software.
Things to look for
- Do you usually receive attachments from this person?
- Is the attachment format the same as previous submissions?
- Is the name of the attachment consistent with prior submissions?
If the answer to any of these questions is no, pick up the phone and call the person directly to confirm the email’s authenticity.
Best Practices when your business receives & opens attachments
- Teach out the SLAM method, or implement a formal Security Awareness Training (SAT) program.
- Implement business-grade endpoint & anti-virus protection like Webroot Business Endpoint Protection.
- Use Google Docs only (Not 100%, but Google has some good anti-virus practices)
- Implement Zero Trust Cyber Security (Full network protection from Phishing & Ransomware)
Message: Does it Make Sense?
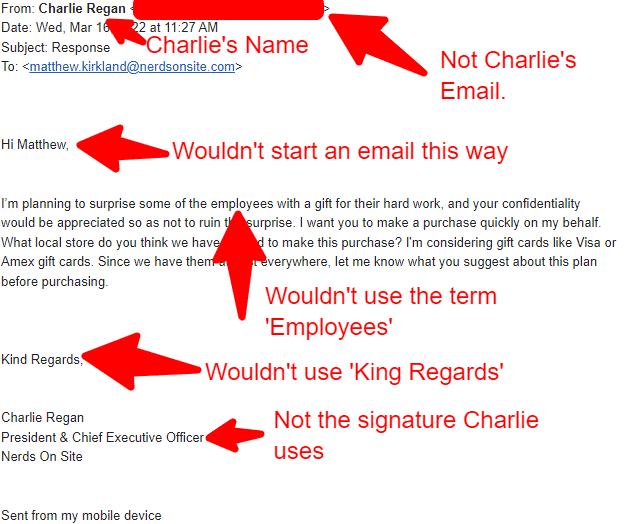
Using another example of Spear phishing I received in March, a cybercriminal emailed me directly asking if I would buy gift cards for a gift for ’employees.’
This email didn’t pass the S as the sender’s domain address didn’t use any of our domain names. This email also didn’t make sense for a few obvious reasons.
- The email didn’t start as an email normally would.
- Different vocabulary than I would typically expect.
- Ending the email with strange wording.
- Not the correct company signature.
When trying to identify phishing emails, you’ll often see examples like this. The best combat method is to pick up the phone and call the person who sent the email to verify.
We completed a Cyber Security Snapshot for a client who had recently been a victim of a data breach, where their email login credentials were compromised. The cybercriminals utilized this information to redirect payments from vendors and customers.
The way the data breach was caught? The attacker used “hey dear” in one of the emails, which wasn’t a usual opening for the administrator. As this didn’t make sense, phone calls were made, the attack was discovered, and remediation took place to rectify the situation.
Conclusion
You now have a good understanding of the S L A M acronym and how to implement it into your business. Phishing is the #1 cause of data breaches and having a plan to prevent phishing attacks should be a top priority.
Nerds On Site is the home of the SME Edge, a complete SME cyber protection package that offers total protection from phishing & ransomware. A full business security infrastructure overall is included and on-going support & security awareness training.