You hear about cyber attacks in the news, but what do they mean for you and your business? This article will break down three of the most common types of cyber security threats and explain how you can protect yourself from them. So whether you’re a small business owner or just someone who wants to stay safe online, read on for helpful tips.
Article Contents
Ransomware
What is ransomware?
Definition (Oxford Languages)
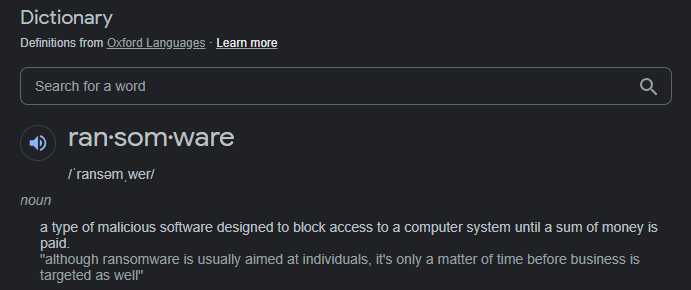
“a type of malicious software designed to block access to a computer system until a sum of money is paid.”
The definition makes it sound quite simple. Well, it is. A few lines of code are designed to encrypt your files and prevent you from using your computer until you pay a sum of money, usually in cryptocurrency.
The most worrying thing about ransomware is that it’s the fastest-growing cybercrime. Between 2020-2021 attacks were up over 150%, with ransom amounts rising over 300%.
While the Oxford Languages definition uses a reference that states it’s only a matter of time before businesses are targeted, we feel that’s somewhat dated. On February 10, 2022, an alert February 10, 2022, by the United States Cyber Security & Infrastructure Security Agency (CISA) stated that ransomware is a national security risk, and ransomware incidents had occurred in 14 of the 16 US critical infrastructure sectors.
When they’re hitting the Government, you know it’s a big problem as Governments often have the most advanced security systems to fend off these types of attacks. Computers weren’t designed to be secure by default. Traditional security systems aren’t excellent at stopping internal action attacks and unknown threats.
For Governments, this should get better over the next couple of years. On January 26, 2022, the Executive Office of the President signed a memorandum requiring agencies to meet specific cyber security standards by the end of 2024, enforcing Zero Trust architecture.

What is Zero Trust
We’re not going to get too deep into Zero Trust in this article, as we could write about it for hours (and we will! Watch our following articles!), but, as you can see above, it’s the way forward for the government. If history teaches us anything, it will be the way forward for businesses.
Long story short, instead of being like a regular computer network where we allow access to everything and block the known bad (and, as mentioned above, we cannot block things like zero day attacks, as they are not known), Zero Trust blocks everything and then only allows the known good.
Shameless plug. Nerds On Site is the home of the SME Edge, a technology co-developed with ADAMnetworks that can protect your home, office, or business against ransomware with AI-driven Zero Trust technology. Currently safeguarding over 2 million devices worldwide, we’ve had 0 ransomware events since 2018.
Phishing Attack
We covered Spear Phishing vs Phishing in-depth with examples in one of our previous articles, so please check it out for a more detailed explanation.
What is Phishing? (#1 Cyber Attack)
Definition (Oxford Languages)
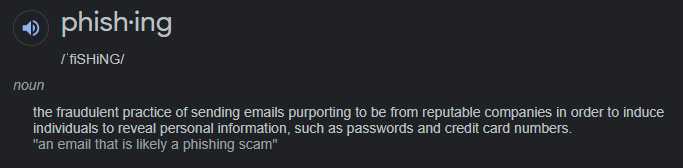
“the fraudulent practice of sending emails purporting to be from reputable companies induces individuals to reveal personal information, such as passwords and credit card numbers.”
Almost everyone with an internet connection has been phished. Cybercriminals send out 3,400,000,000 (3.4 Billion) phishing emails A DAY. That’s 1,241,000,000,000 (1.24 Trillion) emails per year or approximately 156 phishing emails per human.
156 a year. Every single human. If you do some generalized math accounting that only 4.66 billion people are connected to the internet, you can conclude that every connected human gets about one phishing email a day.
I’m going to break that down in the easiest way we can understand. Every human on earth is a victim of a cyber attack every day. We’re ignoring some core variables and have not performed an in-depth study, but if you’ve recently looked at your spam folder and know how to spot a phish, you know this isn’t too far from the truth.
The easiest way to not become a victim of phishing attacks is to know how to spot a phishing email. As mentioned above, we have already written a detailed article on Spear Phishing vs Phishing, and you should take the time to read it.
Credential Theft
Humans are terrible with passwords. We will break down what you should do with passwords and then explain our experiences as a Managed Security Service Provider (MSSP) dealing with Small-and-medium sized Enterprises (SMEs).
Password Complexity
Passwords should be at least 12 characters, including upper & lower case numbers & symbols. According to HiveSystems, a password attack will take over 34,000 years to break this password. In our experience, if passwords take over 4 hours to crack, most (not all) a cyber attacker will stop trying.
Random Passwords
Your password cannot be sequential numbers or common words. It has to be random characters.
Even in 2021, the most used passwords are still 12345, qwerty, password, 111111 & abc123, taking less than one second to crack. Using a simple password is asking for someone to steal data using cyber attacks.
Unique Passwords
Never reuse a password; this includes using old passwords adding symbols/numbers; it must be 100% unique. If we know your old password was SuperNerdMatt, if you change your password, it will be SuperNerdMatt1, or SuperNerdMatt!. Please don’t make it easy for cyber threats to steal data.
Millions of records are lost to data breaches every year, so when a hacker gets one of your passwords and applies the above logic, they may be able to gain access to your other accounts.
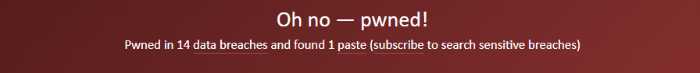
You should do it right now if you’ve never checked if you’ve been part of data breaches.
HaveIBeenPwned is a great tool that records data breaches and the email records that they are a part of. It’s free to use.
It’s worth noting that HaveIBeenPwned will show you what information is available out in the wild (read: leaked on hacker forums). This can often include sensitive data that can lead to identity theft.
I’ve (Matt, the cyber security nerd) been part of 14 data breaches. Some breaches contained general information, and some had passwords and personal information.
Storytime
We’ve got a fantastic story about credential theft that we’d like to share. The story is a few years old now, and if you like listening to podcasts, we highly recommend Darknet Diaries episode 86, “The LinkedIn Incident.”
In 2012 LinkedIn was part of a massive cyber attack. Hackers aimed to steal sensitive data and got millions of user records. Once this sensitive data was out in the wild, cybercriminals tested the logins to see if users re-used passwords.
One of the users of LinkedIn reusing passwords was a Dropbox engineer, and the passwords s/he was using let a hacker gain access to Dropbox and breach 68 Million user records.
Our experience (from cyber attacks)
People typically manage passwords in a very predictable way.
- Use passwords that are not complex.
- Re-use passwords on multiple websites/applications.
- Change passwords by adding something to the end.
We’ve written above why these are bad ideas, but what about those who use complex passwords? This is often how this is managed at home or in an office environment.
- Write passwords down on a per and store them on a desk/on a sticky note/in a draw.
- Save passwords in a file on a computer.
- Save passwords using a browser.
All three of these methods are cyber threats and could allow your credentials to get stolen.
Writing passwords down
Nerds On Site was founded by John Harbarenko & David Redekop as they worked as retail associates at Future Shop in Canada. Matt, the cyber security Nerd, also came from a retail background before joining Nerds On Site. Seeing passwords written on pads of paper, or worse, on sticky notes (visible to customers) was a common occurrence that happened in all stores, in all locations, big or small.
This isn’t just a retail problem; it’s something we regularly see when performing Cyber Security Snapshots in all industries, small offices, healthcare, government, or Fortune 1000. It’s just human behavior.
The problem with writing passwords down is they instantly become insecure. It may not even be available to customers or clients, but it is open to other team members.
Save passwords in a file on a computer (Exposed to cyber threats).
As with above, if you have it noted down, other team members likely know how to access your passwords. Worse yet, when storing it on a computer, any piece of malicious code that enters your computer could steal that information and instantly have one, or all, of your passwords.
Save passwords using a browser (Malicious Code is Scary).
Please don’t do it! It seems convenient, but it is not always secure. Microsoft Edge & Google Chrome have both been targeted by malicious code that steals accounts & passwords from the integrated managers.
What can I do?
There’s only one thing you can do. Get a dedicated password manager.
Password managers can allow for complex & unique passwords for as many websites and applications as you need. The best feature, in our opinion, is that you can often share these passwords with other people in your business without revealing the actual password.
Conclusion
The three cyber security threats we went over are not the only ones, but they are some of the most common. So arm yourself with information and stay safe online. If you need help implementing anything we’ve discussed here, contact Nerds On Site – we’re here to help.












