Cybercriminals are getting more innovative in stealing your data; in July 2022, the Microsoft Threat Intelligence Center posted a detailed threat review of a new type of business email compromise (BEC) that gets around multi-factor authentication (MFA).
Article Contents
Large scale phishing campaign against 10,000 businesses discovered
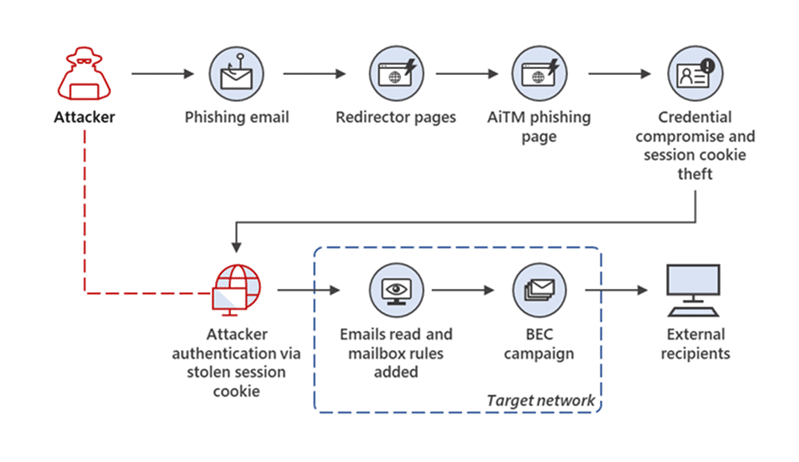
Beginning in September 2021, phishing attacks targeted more than 10,000 businesses, aiming to access victims’ mailboxes. The attackers used a sophisticated phishing technique to bypass MFA.
The attackers created landing pages to subvert the Office 365 authentication process (even on accounts protected by MFA), impersonating the legitimate Microsoft login page. Once the victim’s credentials were entered, the attackers had full access to their Office 365 account – including email, contacts, and calendars.
In several of the recorded incidents, potential victims were sent to landing sites via phishing emails containing HTML attachments that served as the entry point for the attack.
The email would spoof a legitimate email from another user in the organization, often containing an attachment or link to what appeared to be a document stored in SharePoint or OneDrive. When opened, this HTML attachment displayed a login page that looked identical to the Microsoft Office 365 login page.
The hackers who launched these assaults utilized the stolen credentials and session cookies to log into the targets’ email accounts after stealing them. They then exploited their access in business email compromise (BEC) campaigns against other businesses.
“A large-scale phishing campaign that used adversary-in-the-middle (AiTM) phishing sites stole passwords, hijacked a user’s sign-in session, and skipped the authentication process even if the user had enabled multifactor authentication (MFA). The attackers then used the stolen credentials and session cookies to access affected users’ mailboxes and perform follow-on business email compromise (BEC) campaigns against other targets. Based on our threat data, the AiTM phishing campaign attempted to target more than 10,000 organizations since September 2021.”
Read More: From cookie theft to BEC: Attackers use AiTM phishing sites as entry point to further financial fraud.
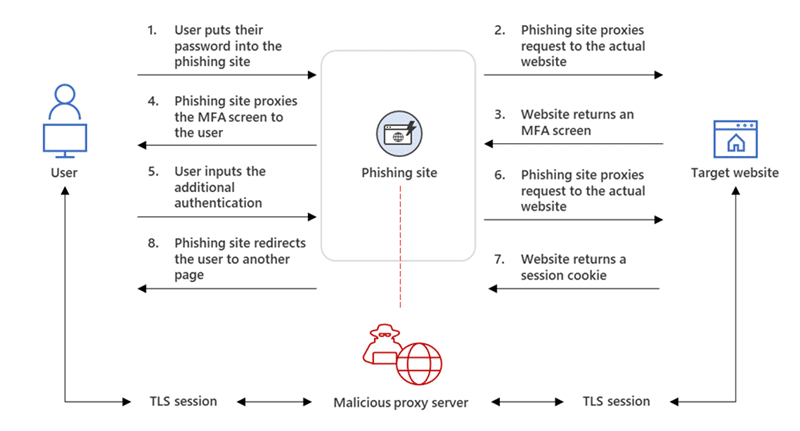
Reverse proxies were used in this attack, and the phishing sites were hosted on web servers that proxied the targets’ authentication requests to the real website they were trying to log in to via two separate Transport Layer Security (TLS) sessions.
The attackers’ phishing page served as a man-in-the-middle proxy, intercepting the authentication procedure to steal sensitive information from intercepted HTTP requests, such as passwords and, even more significantly, session cookies.
After gaining access to the targets’ session cookie, the attackers injected it into their web browser, bypassing the authentication process even if MFA was enabled on the hacked accounts.
What are session cookies?
Session cookies are information that allows a website to track your movements from page to page. They do not stay on your computer permanently and usually expire when you close your web browser.
What is MFA?
MFA is an authentication method that requires using two or more independent factors to verify a user’s identity. These factors can include something the user knows (e.g., password), something the user has (e.g., security token), or something the user is (e.g., biometric characteristic).
What is BEC?
BEC is a cyberattack in which attackers use email to trick victims into wire transfers or sending sensitive information. The attackers often impersonate high-level executives or business partners to add a sense of urgency or legitimacy to their requests.
What is phishing?
Phishing is a type of social engineering attack in which attackers try to trick victims into revealing sensitive information, such as passwords or credit card numbers, or into taking action that will install malware on their systems, such as clicking on a malicious link.
What is an HTML attachment?
An HTML attachment is a file that contains HTML code, which can be used to create a web page. When an HTML attachment is opened in a web browser, the code it contains is executed, and the resulting web page is displayed.
What is a reverse proxy?
A reverse proxy is a type of proxy server that sits between a client and a server. It intercepts requests from clients and forwards them to the appropriate servers. Reverse proxies when used by cybercriminals can be used to conceal the identity of the real server from the client and intercept client information.
What are the implications of this attack?
The fact that attackers could bypass MFA even when it was enabled on the accounts they compromised highlights the importance of using strong passwords and not reusing them across different sites.
In addition, organizations should be aware that phishing attacks are constantly evolving and must keep up with the latest trends to protect their employees and customers best. The use of reverse proxies in this attack also highlights the importance of monitoring network traffic for unusual activity.
Defending against this kind of attack
Microsoft recommends MFA solutions that utilize Fast ID Online (FIDO) v2.0 and certificate-based authentication, along with conditional policies on your MFA solution & anti-phishing tools.
We recommend utilizing a zero trust security approach and not solely relying on MFA to protect your organization.
Zero Trust Network Security
Utilizing the SME Edge, businesses can block all unknown IPs and websites by default, meaning this attack could not have been possible.
SME Edge provides a Zero Trust security posture for businesses of all sizes, without the need for expensive and complex solutions. We make it easy to stop data exfiltration, phishing, and other types of attacks with our patented AI user and entity behavior analytics (UEBA) engine that analyzes traffic data in real-time to identify and block all malicious activity.
There have been no recorded events of SME Edge clients having instances of breaches or data loss.