What is Cybersecurity?
UK-based internet security company IT Governance tells us that “Cyber security is the application of technologies, processes, and controls to protect systems, networks, programs, devices and data from cyber attacks.”
Article Contents
A comprehensive cybersecurity plan aims to reduce the risk of cyber-attacks and protect against the unauthorized exploitation of operating systems, sensitive data, networks, and technologies.
Every business implementing internet services must create a security culture to improve business and consumer trust.

small business cyber security
Has COVID-19 Affected Cybersecurity?
Cybercrime, which includes everything from theft or embezzlement to data hacking and destruction, is up 600% due to the COVID-19 pandemic. Nearly every industry has had to embrace new solutions, and it forced companies and government agencies to adapt quickly and take cybersecurity strategy very seriously.
Do Small Business Owners Need to Worry About Cybersecurity?
The answer is a resounding, unequivocal YES!
Everyone who logs on to a computer needs to worry about cybersecurity. Many small business owners believe they are too small for the hackers to worry about and don’t have enough data to warrant a breach. This is not true. Small businesses are not just one target of the bad guys; they are a favorite target.
10 Small Business Cybersecurity Statistics That Should Scare You.
A 2021 report from fundera by nerdwallet revealed that:
- 43% of cyber attacks target small businesses.
- 60% of small businesses victims of a cyber attack go out of business within six months.
- Cybercrime costs small and medium businesses more than $2.2 million a year.
- There was a 424% increase in new small business cyber breaches last year.
- 3 out of 4 small businesses say they don’t have the personnel to address IT security.
- 54% of small businesses think they’re too small for a cyber attack.
- Small businesses spend an average of $955,429 on restoring regular business in the wake of successful attacks.
- 50% of small and mid-sized businesses reported suffering at least one cyber attack last year.
- Small businesses spend an average of $955,429 on restoring regular business in the wake of successful attacks.
- 91% of small businesses don’t have cyber liability insurance.

small business cyber security
Why are Small Businesses a Favorite Target for Hackers?
There are several reasons small businesses can become preferred targets for cybercriminals. First, there is this kind of head-in-the-sand thinking we’ve talked about where small business owners don’t believe they can be targets for data systems breaches and so don’t spend the time or money necessary to defend themselves properly.
Don’t fool yourself—even your tiny bits of data – credit card numbers, medical records, bank account information, etc. – are easy to unload on the dark web with the proper internet browser. And they’re not just hacking you; they’ve targeted hundreds, maybe thousands of others – so you do the math.
Don’t Have the Time, the Money, the People
Then there is the problem that so many people involved in small businesses don’t have the resources to implement adequate security systems. And with fewer resources dedicated to the advanced security necessary to protect your small business, there are bound to be some security measures that get overlooked. According to fundera by nerdwallet, we see that 47% of small businesses say they have no understanding of how to protect themselves against cyberattacks, and 3 out of 4 small businesses say they don’t have the personnel to address IT security.
Start Small to Go Big
Today’s companies are digitally connected to facilitate transactions, manage supply chains and share information. Since larger companies presumably, though not necessarily, are t0ugher to hack into, the cybercriminals target smaller partners as a way to get into the systems of large companies.
What’s at risk?
A cyberattack can drastically impact your business. As cited above, 60% of small businesses that fall victim to an attack shut down within six months of the breach. While that may be the most devastating result of an attack, there are other consequences that your business could experience, like losing your customers’ confidence and besmirching your brand’s reputation.
You could be giving away:
- Client lists
- Customer credit card information
- Your company’s banking details
- Your pricing structure
- Product designs
- Expansion plans
- Manufacturing processes
And it’s not just you that they can affect
These attacks don’t just put your company at risk for a data breach. Hackers may use their access to your network as a stepping stone into the networks of other companies whose supply chains you’re part of—all very difficult to recover from.
And then there are the bucks
In terms of dollars, Sophos, a British-based security hardware and software company, estimates the average cost of recovering from a ransomware attack was $1.85 million in 2021.
Cybersecurity for Small Businesses
What Type of Cyber Attacks Go After Small Business?
4 Common Security Threats
1. Spyware
Spyware is software that infects your PC or mobile device. It gathers information about you, monitors your browsing and Internet usage habits, and collects other data—it’s a total invasion of privacy.
That’s some sneaky software.
Running quietly in the background, spyware can steal your internet history, contacts, passwords, and even credit card information. In the cases of smartphones and tablets, it can steal information such as:
- Incoming/outgoing SMS messages
- Incoming/outgoing call logs
- Contact lists, emails
- Browser history
- Photos
Spyware is clever, making its way onto your computer without your knowledge or permission, attaching itself to your operating system, and maintaining a presence on your PC. The problem is it can be challenging to detect. If your device is infected, you might see a significant reduction in processor or network connection speeds, increased data usage, and low battery life.
Spyware can infect your system in the same way that other malware does.
Here are a few ways spyware can make its way into your device:
- Security vulnerabilities like clicking on an unfamiliar link or attachment in an email.
- Installing “Useful Tools” from third parties. Spyware authors often present their spyware programs as tools to download, like an Internet accelerator, download manager, or hard disk drive cleaner. But be careful. Installing this malicious software can result in spyware infection.
- Software bundles. Free software can conceal a malicious add-on, extension, or plug-in.
2. Ransomware
Ransomware is another form of malware. There are several things this form of malware can do once it has taken over your computer. Most commonly, your files become encrypted, making them inaccessible to you and your team.
An excellent argument for backing up files
The files can’t be decrypted without a key that is only known to the hacker—users are given instructions for how to pay a fee (usually in the form of cryptocurrency) to get the decryption key.
A less common type of ransomware, called leakware or doxware, is when an attacker threatens to publicize sensitive data on the victim’s hard drive unless a ransom is paid.
Ransomware most often infects a device with phishing or smishing scams. Other less common ways it reaches a device is through holes in your security.
3. Distributed Denial of Service (DDoS) Attacks
Significant threats to business operations.
These attacks target websites and online services to overwhelm them with more traffic than they can handle. This makes the website or service inoperable, resulting in a denial of service to legitimate users or customers.
Downtime is no good for dollars
The targeted websites or services are bombarded with incoming messages, requests for connections, or fake packets. Attacks are launched from any number of corrupted computers, from a few to thousands.
Since the attack comes from so many different IP addresses simultaneously, a DDoS attack is much more difficult for the victim to locate and defend against. This is part of what makes DDoS attacks such a problematic cybersecurity threat.
DDoS or something more malicious inside?
Disturbingly, a DDoS attack might be just the tip of the iceberg. These types of attacks can be used to hide other malicious activity. With your IT security team distracted by the DDoS attack, who knows what other malicious activities the bad guys have going on in the background?
4. Phishing
Phishing is an online scam where criminals send an email that appears to be from a legitimate company and ask users to provide sensitive information.
This type of scam could grant the attacker access to all sorts of valuable data—so you must know how to spot such an attack.
Here are a few things you should be on the look-out for:
- The displayed name in the email – A name displayed in the “from” box does not guarantee that it came from this sender.
- Suspicious links – If the web address you see when you hover over the link doesn’t seem to match the sender, don’t click. Be wary if an email directs you to a website asking for a login.
- Spelling or grammar mistakes – If it doesn’t look or sound right, it’s probably not legit.
- Odd salutations – If the contact usually addresses you by name, but the email uses something generic like “Valued Customer” or “Important Client,” this is a red flag.
- Request for sensitive information – If you’re asked for confidential information you aren’t comfortable sharing, pick up the phone and call a verified number to confirm the request.
- Implied urgency – This is a scare tactic designed to catch you off-guard and reply when you usually wouldn’t. If someone threatens to stop a service without an immediate reply, stop and think about it (and contact your tech nerd).
- Broken images or format – If the images or layout of an email seem a bit off, it could be a sign this is an attempt to fool you.
- Suspicious domains – Malicious emails routinely use parts close to the legitimate domain, but not quite right. For instance, someone may use Capital0ne.com instead of capitalone.com to try luring you into providing your credentials.
- Non-standard attachments – if the attached file is not one you recognize (like .doc for a Word file, .xls for an Excel file, or .pdf for a PDF file), be suspicious (and don’t open).
6 Ways to Protect Your Data and Connected Devices from Cyber Attack
- Make security part of your company culture. Be vocal about the importance of cyber security across the entire organization. Let all departments know that cyber security is a high priority
- Train your people. This is part of creating a culture of security. Employees can leave your business vulnerable to an attack. Research shows that 43 percent of data loss stems from internal employees who maliciously or carelessly give cybercriminals access to your networks.
- Deploy antivirus software – and keep it updated. It would be best to have antivirus software to protect your devices from viruses, spyware, ransomware, and phishing scams. Make sure it is updated regularly to strengthen it or add patches.
- Utilize VPNs and Firewalls. These defense lines can’t prevent all types of attacks, but they are highly effective when implemented properly
- Back up, back up, back up. It’s always a good idea to have multiple backups of your business’s data. That way, if you’re ever the victim of cyber threats, a ransomware attack, a natural disaster, or some other event that restricts your ability to access your data, you’ll have a backup plan to protect your small business.
- Limit employee access. It makes sense to segment and limits employee access to only the systems and data they need access to. If you maintain tight controls over user access, you’ll limit the damage that any single user (or compromised account) can do to your network security.
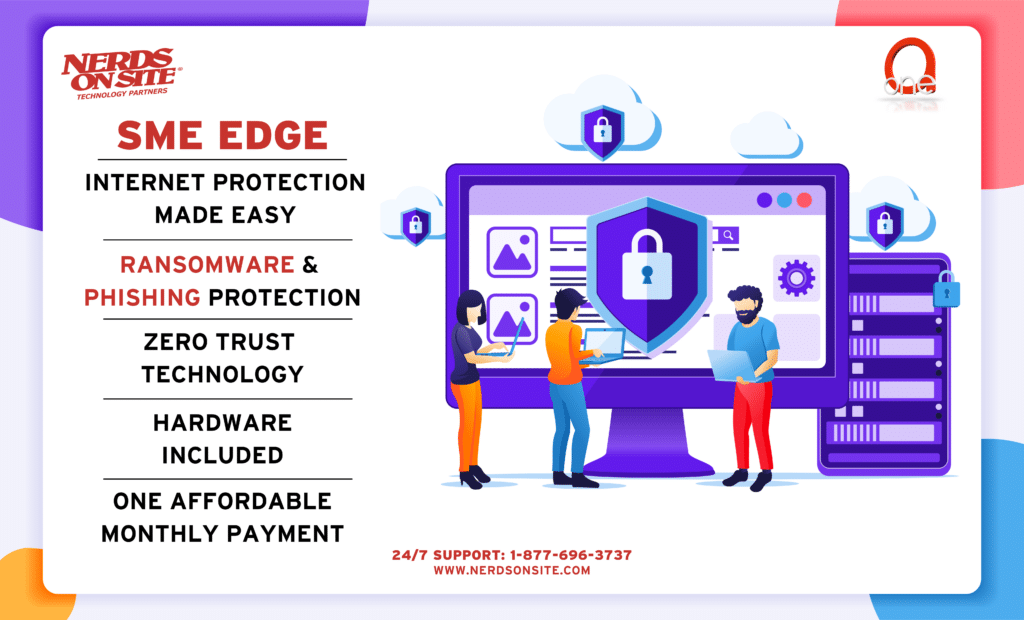
Nerds On Site SME Edge
Time to face facts
Big business, small business, mom and pop shop. If you’re in business, you need to make cyber security a part of it. Chances are high, nearly certain, that you’ll be attacked. But with the right security policies technology, cyberattacks should be caught before they get anywhere near encrypting files and extorting small business leaders. And while basic security practices risk assessment that is likely not your specialty, there is always a Nerd ready to help you with cybersecurity for small businesses.
Nerds On Site has a global team of experts with solutions that can protect your business from any cyber threats. From first steps to advanced protection, we have you covered. Call us today for more information.